In the past, protecting and securing enterprise data was simpler—handled mainly through the use of basic perimeter-based devices like firewalls and intrusion protection services. As more and more enterprises now look to migrate or augment their big data clusters with the cloud, the amount of access points to their data continues to exponentially increase. For the modern enterprise, perimeters are almost gone. Thorough security and compliance measures for this newly distributed data are now a top priority for CISOs and security teams, well-covered in several recent articles around the web. Here are the common themes, along with some tips on how enterprises can adapt quickly to enable public cloud benefits while minimizing corporate risk.
Cloud’s Faulty Security Reputation
Along with the public cloud’s benefits and potential risks comes concern about security vulnerabilities. Our 2014 cloud survey with GigaOm found that 63% of companies were most concerned with security and breaches as barriers to cloud usage. This concern was understandable, with the multitude of potentially disastrous data breaches being exposed in recent years. Yet the blame for these vulnerabilities is often wrongly placed on the cloud providers—lending to the flawed reputation of inadequate cloud security. Gartner investigated this misplaced blame among cloud security incidents, and found that a small percentage of them were actually the cloud provider’s fault. The study predicts that through 2020, 95% of cloud security failures will be the fault of the customers – not cloud providers.
Confidence in Public Cloud Grows
In Prat Moghe’s TNW article 6 hidden challenges of using the cloud for big data he dives deeper into the idea of human mismanagement in cloud, affirming that experts agree on cloud providers being the most secure they ever have been—more secure than on-premises data centers with cloud offerings like AWS and Azure. Even the most security-conscious industries like financial services and healthcare have begun utilizing the public cloud. A 2016 RightScale survey found a divergence, or perhaps evolution, in cloud opinion from our 2014 GigaOm study, showing that a ‘lack of resources/expertise’ had replaced security as the biggest challenge with cloud. The modern cloud climate lends itself to the notion that issues with cloud security can often be chalked up to results of inconsistent use or poorly-defined policies.
The Next Challenge: Integrating the Enterprise Cloud
Another new challenge that enterprises must address, along with secure user management, is the integration of cloud resources with existing on-premises data infrastructure. Integration is important to avoid data silos—where stand-alone repositories of data become isolated and create barriers for enterprise agility and decision-making. At Equifax, for example, CISO Susan Mauldin and her team treat the cloud as another enterprise asset to be secured. This means that up-to-date patches and compliance certifications must be maintained, and vulnerability assessments and penetration tests should be regular.
Enterprise Cloud Checklist
In observing how enterprises have approached these challenges, a few common tips emerge for locking down the cloud:
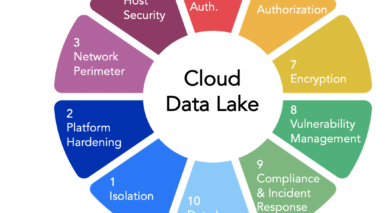
• Data should be encrypted both at-rest, through an HSM-based key management –and in-motion, with either IPSEC or SSL depending on the enterprise’s firewall configuration.
• A security gateway or dedicated VPN tunnel should be in place to block all external cloud access from outside of the enterprise.
• Role-based access controls should be layered on the cloud to define authentication and restrict any unauthorized activity or access.
• A mobile data management plan should be in place and account for emergency situations of theft or loss.
• Finally, all data in the cloud should be logged, audited and tracked to allow for organized inventory and security monitoring and alerting. The logs should be normalized across data services, and all events should integrate with the SIEM environment.
Your Enterprise’s Path to Success
To establish and implement these policies is a large feat for enterprises. It may become necessary to invest in resources or new skills to bridge the security gap, and more intelligently wield the wide array of security tools that cloud providers offer. But with careful assessment, your IT security team can conquer these challenges and safely leverage cloud platforms.
For more information on the comprehensive security provided by Cazena’s managed Big Data as a Service, please contact us today.